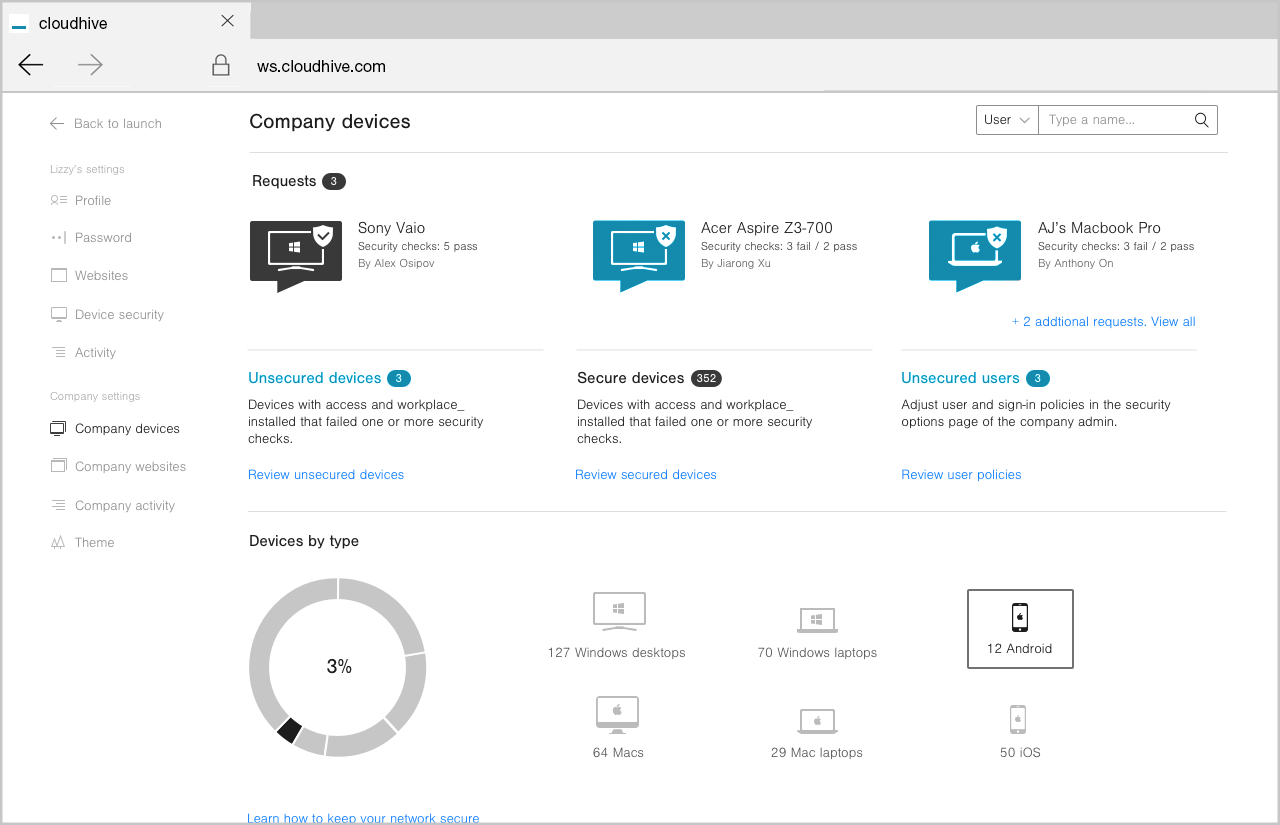
Total control of Access is at your fingertips
You want your users to have the ability to access the files and apps they need, but you want control on which devices they use for that access.
One of the best things about Cloudhive is that it enables end-users to ‘bring your own devices’ (BYOD) giving them the opportunity to work anywhere, anytime. But you still need to be able to manage what devices they use to gain access.
Each time a user attempts to log-in on an unrecognised device you will be notified and you can ensure the device has the appropriate levels of security on it before approving access.
It only takes a few seconds to allow or disallow a device, but it gives greater piece of mind knowing your company’s assets are protected from the ground up.